In this blog post, we'll explore Amazon Elastic Compute Cloud (EC2), an indispensable AWS service that provides scalable computing capacity in the cloud.
We'll delve into the details of instance types, launching instances using Amazon Machine Images (AMIs), and configuring security groups for network access control. This comprehensive understanding will empower you to effectively harness the capabilities of EC2 for your diverse workloads in the cloud.
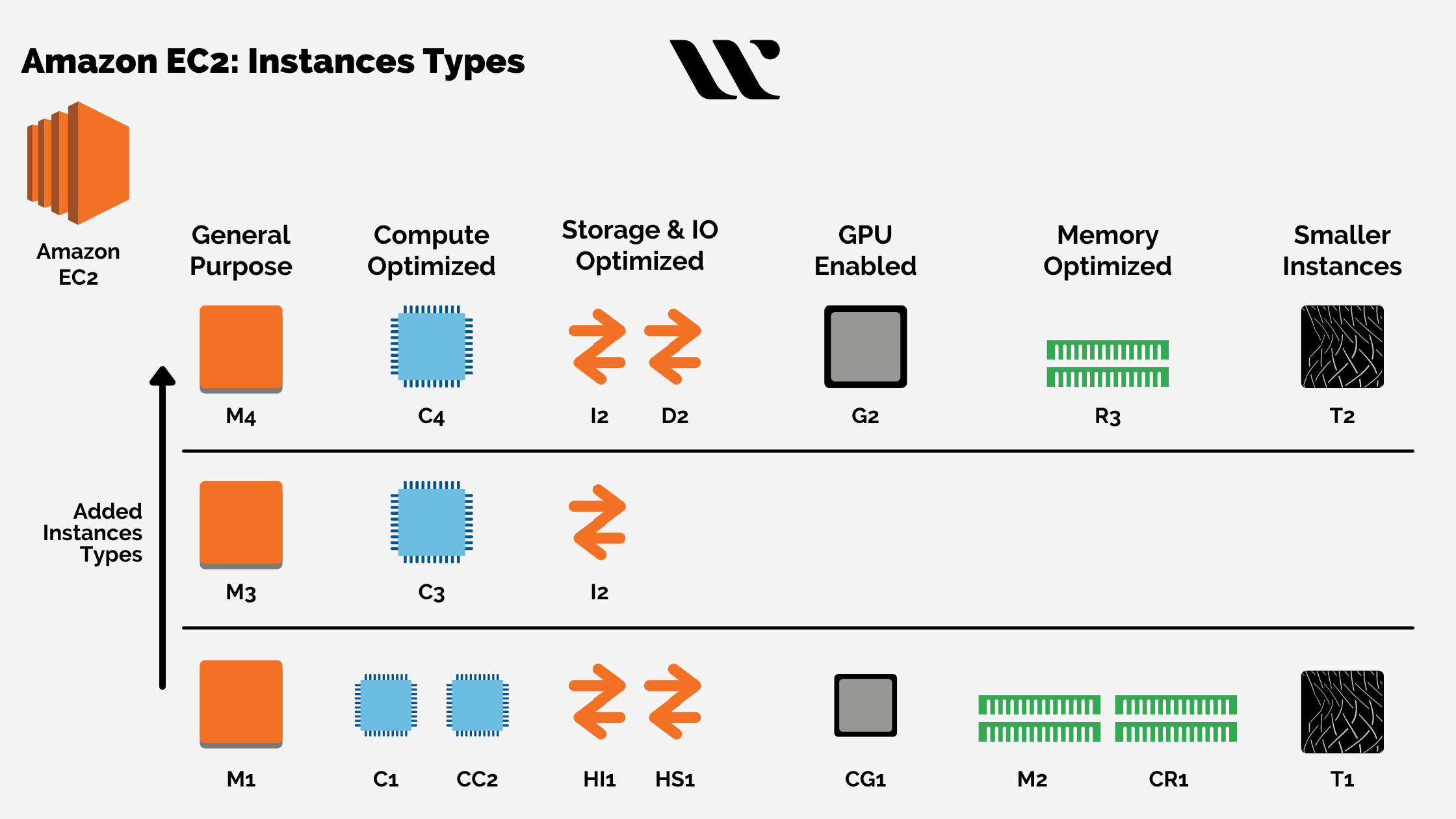
1. Instance Types and Their Significance in Workloads
Amazon EC2 offers a diverse spectrum of instance types, each uniquely designed to cater to distinct workloads. Understanding the nuances of these instance types is pivotal for optimizing your cloud infrastructure.
Instance Types Demystified:
- General Purpose Instances (e.g., t3, m5): Ideal for versatile workloads such as web servers, small databases, and development environments due to their balanced compute and memory resources.
- Compute Optimized Instances (e.g., c5): Tailored for CPU-intensive tasks and high-performance computing.
- Memory Optimized Instances (e.g., r5): Crafted for memory-intensive applications like in-memory databases or data analytics.
- Storage Optimized Instances (e.g., i3): Tailor-made for storage-intensive applications like NoSQL databases and distributed file systems.
- Accelerated Computing Instances (e.g., p3, g4): Leverage specialized hardware like GPUs for machine learning and graphical rendering tasks.
Application in Varied Workloads:
- Consider the specific needs of your workload concerning CPU, memory, storage, and specialized hardware, and align them with the appropriate instance type for optimal performance and cost-effectiveness.
2. Launching Instances using Amazon Machine Images (AMIs)
Step-by-Step Instance Launch with AMIs:
1. Access the AWS Management Console and navigate to the EC2 Dashboard.
2. Click "Launch Instance" to initiate the instance creation process.
3. Choose an AMI that aligns with your specific requirements (Amazon Linux, Ubuntu, Windows, etc.).
4. Select the instance type that suits your workload's demands.
5. Specify the number of instances, network settings, storage, and other relevant details as needed.
6. Configure Security Group: Establish rules for inbound and outbound traffic (detailed below).
7. Review configurations and initiate the instance launch.
---
3. Configuring Security Groups for Network Access Control
Steps for Effective Security Group Configuration:
1. Access "Security Groups" from the EC2 Dashboard.
2. Initiate a New Security Group: Click on "Create Security Group."
3. Define inbound and outbound traffic rules, including type, protocol, port range, source/destination (IP or other security groups), and descriptions.
4. Apply the relevant security group to instances during launch or management.
5. Regularly reassess and update security group rules to match evolving security needs.
---
The Vital Role of Security Groups
Why Security Groups are Essential:
1. Ensures controlled inbound and outbound traffic, crucial for securing EC2 instances and governing data flow.
2. Provides firewall functionality, allowing or denying traffic based on established rules to mitigate unauthorized access risks.
3. Offers granular control by providing detailed rules based on protocols, ports, and source/destination IP addresses or security groups.
4. Acts as a protective shield around instances, permitting only designated and necessary traffic.
Inbound and Outbound Rules Management:
- Inbound Rules: Dictate allowed traffic to reach instances (e.g., permitting HTTP/HTTPS traffic on ports 80 and 443 for web servers).
- Outbound Rules: Govern originating traffic from instances, defining what the instance can access.
Significance in Cloud Security:
- Reduces the risk of unauthorized access and potential security breaches by allowing only essential traffic.
- Enforces adherence to security best practices and ensures only essential services and ports are accessible.
- Allows for rule modifications in response to changing traffic requirements and evolving security threats.
---
Conclusion
Understanding the core functionalities of Amazon EC2 - instance types and their applications, launching instances with AMIs, and configuring security groups - equips you with the essential knowledge to efficiently and securely utilize EC2 for diverse workloads in the cloud. This comprehensive understanding positions you to leverage the full potential of EC2 in your cloud endeavors.